For things to change, we need to change the way we address security. By not doing so, we risk the insecurity of the entire digital world with global economic repercussions.
What do the following, recently cyberattacked organizations have in common:
SunWater, Media Markt, the FBI, the Department for Transport and Ikea? Apart from all suffering cyberattacks in the last few weeks, all have been exploited due to maintaining suboptimal websites and servers. These insecure websites and servers were subsequently identified, infiltrated, and either command and control (C2) was taken, or data was exfiltrated, including personally identifiable information (PII).
I wrote an article on Survivorship Bias last year. In it, I outline how in 1943, Abraham Wald hypothesised that it was not the damaged surface on planes that were shot at, but rather the damaged surface on planes at the bottom of the sea with holes in the engines that needed hardening. Abraham Wald’s genius finally convinced the US Air Force to strengthen the correct surface areas. Many more planes made it home safely after that.
Suffering from Cognitive Bias
Fast forward to 2021, and we still suffer from the same bias.
Let’s look at some of the organizations that are at the ‘bottom of the sea’ due to being exposed and susceptible to cyberattacks that would fatally wound them.
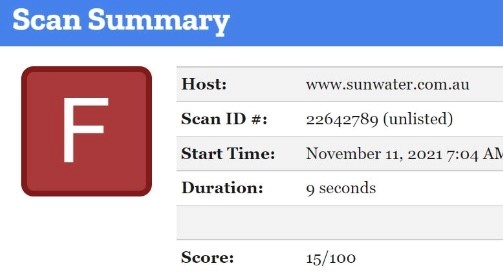
SunWater, the Australian Government owned Critical National Infrastructure water provider, suffered a cyberattack that was later found to have lasted a full 9 months before even being noticed. This confirmed that their digital security lacked controls and management. Furthermore, although a typical discovery of digital infiltration is circa 6 months, we should not forget that SunWater is both a government organization and a CNI organization providing essential water to a large populace. Given the Oldsmar water cyberattack earlier in the year acting as a clear warning, SunWater decided to ignore that lesson and allowed themselves to be compromised and exploitable due to inadequate security.
The below Cyber Rated Index (from CIP) shows an F rating, the worst possible rating which takes many known website exploits into consideration, including OWASP’s top ten, Mitre CWE and HackerOne. The Domain Name System below the CRI shows a very concerning 6 insecure servers, insecure delegation status, and two errors in red and one warning in yellow.
Media Markt is Europe’s No 1 electrical retailer and suffered a near total shut down over the last several weeks. The Infiltration was so bad that executives were running around screaming to their employees to disconnect everything from the internet. Media Markt is a multi-billion Euro company and is struggling through this attack. However, the attack was almost a self-fulfilling one as their suboptimal security position made them a sitting duck.
Media Markt are also guilty of the digital cardinal sin of displaying the dreaded ‘Not Secure’ indicator on their homepage. This confirms to the world that they are a target since HTTPS was enforced by Google and other ISPs in 2018 and any website with suboptimal, and easily hacked HTTP, would display the International Sign of Insecurity: ‘NOT SECURE’.
A ‘Not Secure’ sign is like a calling card for cybercriminals and confirms the website lacks basic security, and data is in plain text and not cipher text (including PII) data. Think about this for a moment, Media Markt, due to COVID, has seen a very high percentage, near all sales online over the last two years, all whilst having ‘Not Secure’ websites.
It goes without saying that Media Markt’s CRI and DNS positions are also poor and provide numerous attack possibilities for a cybercriminal with just a modicum of website offensive capabilities.

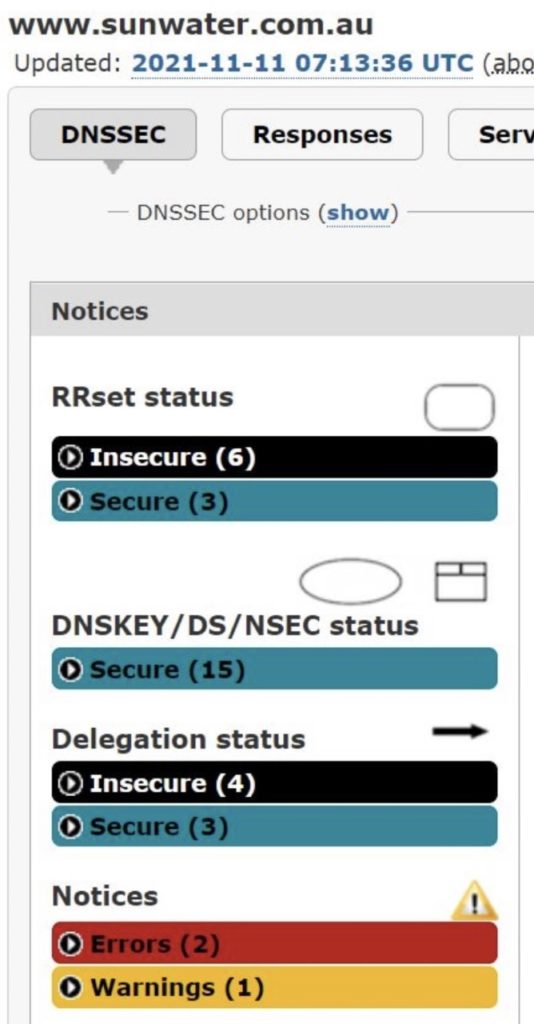
The Federal Bureau of Investigation itself suffered a rather embarrassing cyberattack just weeks ago whereby cybercriminals gained access to FBI servers and sent a bogus FBI email to around 100,000 recipients alerting them to a cyberattack in flight. It is unclear at this point what other intrusions or malware might have been planted or used in the emails, however, the spoof emails were so well-constructed that they would have been received and opened with complete belief they were from the FBI and provided factual intelligence, resulting in any links or malicious code being readily accepted.
These are smart people – smarter than average.
The example below is one of several we found without too much effort and confirms 2 DNS Insecure servers, a delegation issue and no less than 12 warnings. This particular domain also has SSL issues which made data lack integrity, the website lacked authentication, and data in flight to be unencrypted, i.e. in Plain Text, a cybercriminals Shangri la. Simply put, these exposed, easily exploited websites and servers are just too much not to take a swipe at for a cybercriminal with little to no attribution. It is also obviously quite a trophy.
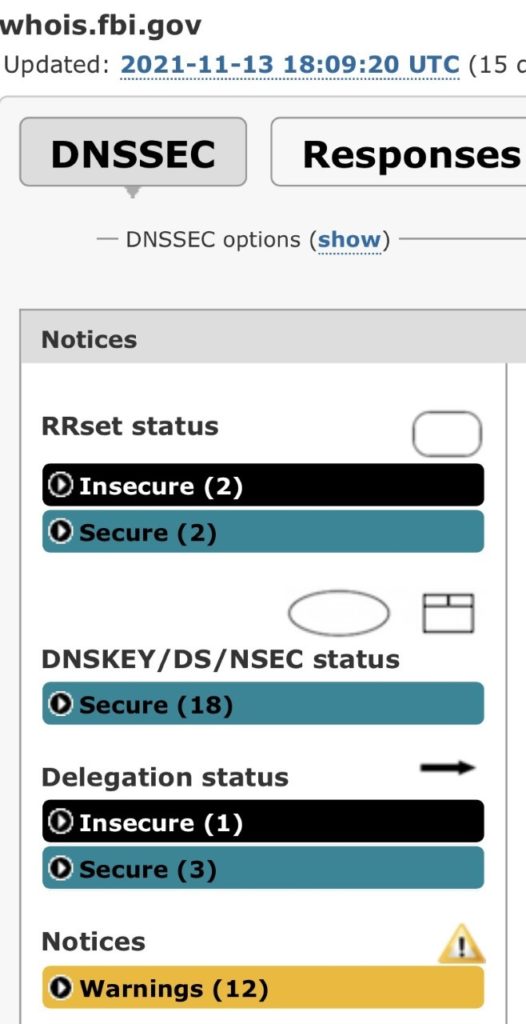
Last week the Department for Transport, the UK government’s department for all Transport related matters, had a rather embarrassing digital infiltration which saw their website, www.charts.dft.gov.uk, which provides data and information for various transport-related bodies, taken over and used to stream pornography to any website visitor. The website and servers had been taken over and commandeered, completely unknown to the DT employees and security team, and in turn their government, until they were alerted to the streaming.
We looked at the DT’s PKI, CRI and DNS position and discovered, once again, an insecure position and in some cases, a complete lack of security, making this, as with a vast number of cyberattacks, even more opportunistic than sophisticated and targeted attacks.
In addition to SunWater and the FBI, this made the third attack on government websites and servers within as many weeks. The DNS below confirms insecure servers, delegation and warnings, which are all evident, and thus, easily exploitable.
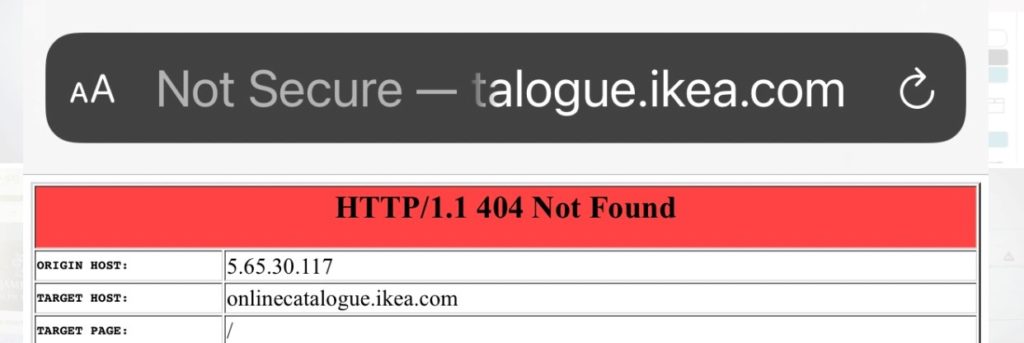
This week the global ‘flat pack’ and furniture company IKEA suffered a massive cyberattack that used internal servers to compromise and send emails seemingly to and from members of staff, complete with malware attached.
The emails appeared just like those sent and received from the FBI, fully bonafide.
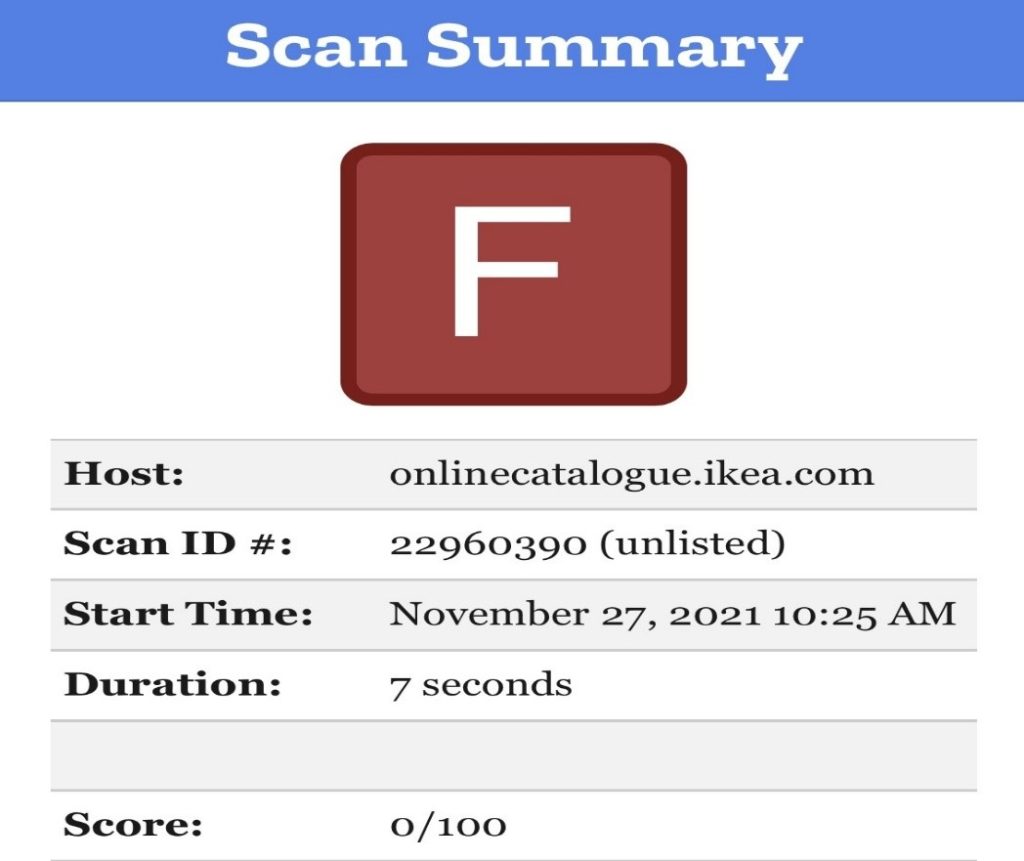
CIP investigated immediately after being made aware and have a complete analysis being published next week in CyberTheory’s weekly guest blog post and on the ISMG network. What we discovered was a systemic set of security errors. Some dated as far back as pre-2010 and including ‘Not Secure’ subdomains, suboptimal CRIs, DNSs and PKI issues in abundance.
This attack has, not surprisingly, spread like a pandemic, even quicker as it almost immediately gave rise to knock-on attacks to partners, suppliers and customers.
Without being too dramatic, such events can, and often do, topple companies.
The ‘Not Secure’ IKEA website below has been ‘Not Secure’ and using HTTP since it was replaced in 2018. An almost certain guarantee of when, not if a cyberattack occurs.
This article is not meant to embarrass or provoke condemnation of these organizations, but rather to highlight their lack of controls of internet connected websites and servers as being a major catalyst for being targeted and attacked.
It is meant to urge organizations to address the systemic root cause for much of today’s Digital Pandemic in much the way that Abraham Wald taught Survivorship Bias to the U.S. Air Force back in 1943. Alan Turing, who was also thought of as a ‘loose cannon’ in many circles, saved hundreds of thousands of lives by developing The Bombe, an electro-mechanical device used by British cryptologists to help decipher German Enigma-machine-encrypted secret messages during World War II.
That invention arguably led William Tutte, an English and Canadian codebreaker and mathematician to discover and break the Lorenz cipher, a major Nazi German cipher system which was used for top-secret communications within the Wehrmacht High Command.
Without that achievement, Normandy would have turned out quite differently.
Looking in the Wrong Places
Governments, and people, even the Intelligence Community, appear to be simply looking in the wrong places instead of where actual digital intrusions are occurring. They keep looking at the holes in the airplanes and not at creating more resilience and strength where it is really required.
CISOs, executives and security professionals are in denial of their insecure websites and appear more concerned about exposing themselves for fraudulently providing security, than about assuring actual security. This results in many cyberattacks being characterized as ‘sophisticated’ in an attempt to distract from internal incompetence and lack of basic, fundamental security.
Furthermore, when a company like the Bank of America proudly declare they spend $1 billion on security, and we show them one of their UHNW customer login websites is ‘Not Secure’, exposed and easily exploited, they are not interested in this discovery becoming public, and react by attending to this very real threat as if it were a software vulnerability that needs patching.
Fortunes are being spent and lost to cybercrime.
The global economy is suffering astronomical losses while those responsible for security continue looking in the wrong direction. When Abraham Wald first declared the U.S. Air Force were wrong to suggest the bullet holes were where planes should be reinforced, we are simply stating a similar set of facts.
You can look anywhere you prefer, however, unless you address the area where a network is connected to the internet – your websites and servers – organizations, just as the airplanes that were not correctly reinforced, will continue to get shot down.
